Dear GIFCT Stakeholders,
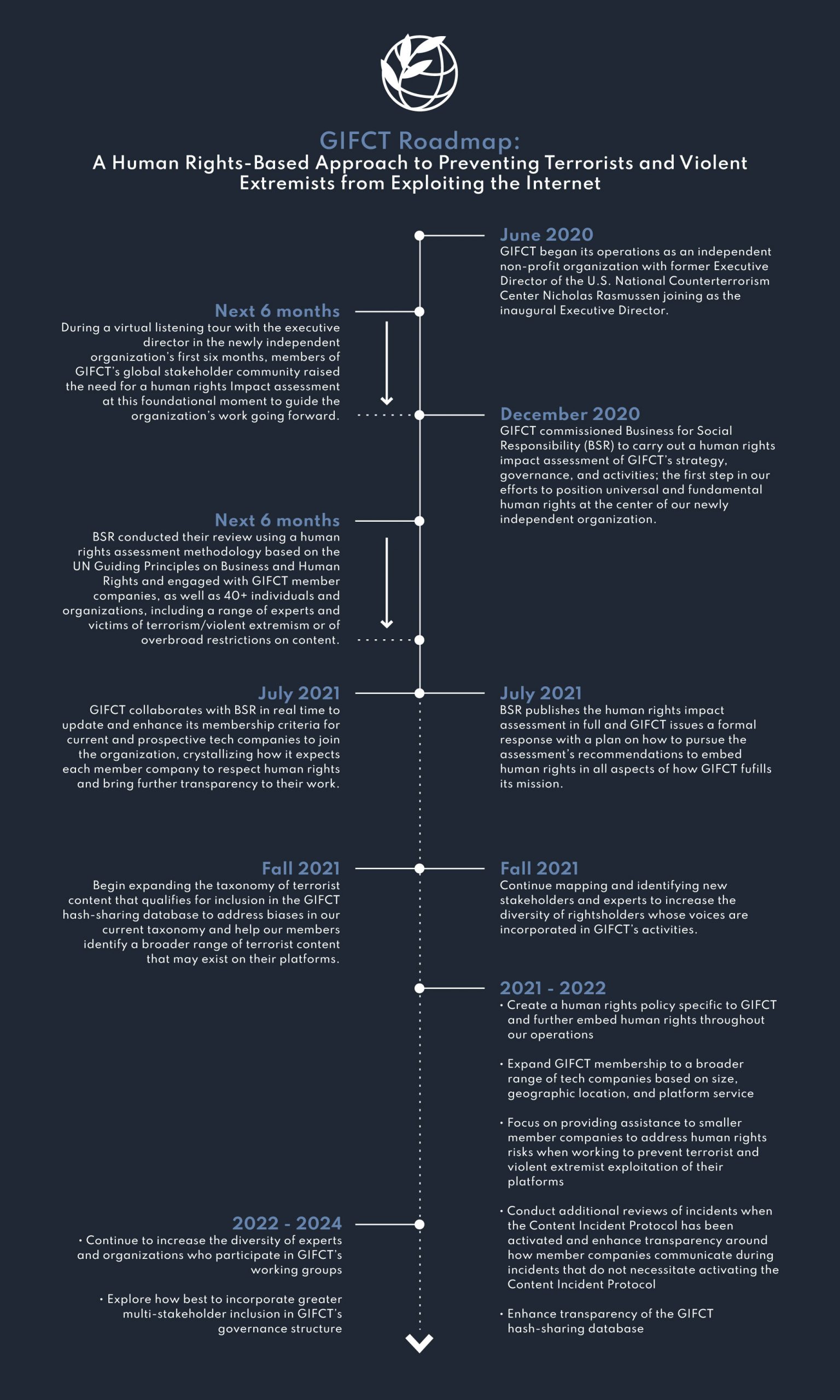
One year ago, when I assumed the role of inaugural Executive Director of the Global Internet Forum to Counter Terrorism (GIFCT), I embarked upon a six-month virtual listening tour with members of our global stakeholder community. As part of that process, I met with colleagues from industry, government, academia, and civil society about both the challenges and opportunities for GIFCT as a newly independent organization.
In my conversations with a range of civil society stakeholders — members of our Independent Advisory Committee, participants in our working groups, and other individuals following and invested in GIFCT — understanding and addressing the human dimension of the impacts of our work emerged as a key theme. In particular, I received advice to focus on those most vulnerable in this context: both the victims of terrorism and violent extremism and the victims of efforts to address terrorism and violent extremism.
Drawing on recommendations from multiple quarters, I committed last fall to commissioning an assessment to identify in detail the actual and potential human rights impacts of GIFCT’s work. My hope was that this report would serve as a catalyst for GIFCT’s organizational development as a newly independent entity, helping us at this foundational moment to chart a clear path forward for the coming years. The Operating Board also reaffirmed its commitment to conducting this assessment and ensuring that the protection of human rights and free expression remain a cornerstone of GIFCT’s work.
In December, GIFCT partnered with a non-profit organization called BSR (Business for Social Responsibility) to conduct the assessment. Over the past six months, this effort has informed our work in real-time, allowing us to take early and decisive action to position universal and fundamental human rights at the center of our strategic planning and programmatic activities. Today, I am pleased to share that we have published BSR’s full report on our website here. We plan to hold open office hours this afternoon for anyone interested in an informal conversation with us about the recommendations and look forward to addressing some of the key questions and topics of interest that emerge at a panel discussion focused on the assessment at our Global Summit next week.
While BSR’s assessment focused on identifying and making recommendations to address possible adverse human rights impacts, the report also emphasizes the potential of GIFCT to facilitate the realization of human rights, including to life, liberty, security, and freedom of expression, among others. We take this positive responsibility seriously. After months of interviews with a diverse and global set of GIFCT stakeholders, BSR has offered a series of recommendations on how to pursue rights-respecting approaches to achieving our mission of preventing terrorists and violent extremists from exploiting digital platforms. As a starting point, we outline in the roadmap below the commitments we intend to make over the short, medium, and longer term.
The Recommendations
Based on conversations with 40+ individuals and organizations across our stakeholder community, BSR offered 47 concrete recommendations to GIFCT that spanned nine themes and 35 questions, to include membership, organizational governance, content removal and preservation, and consideration of terrorist and violent extremist content, among others.
1. Current Commitments
As BSR’s insights helped inform our work in real-time, we have already made significant progress towards implementing numerous key recommendations. On membership, in particular, we collaborated with BSR to refine our guidelines for companies interested in joining GIFCT. The purpose of these enhanced criteria — now available on our website here — was threefold: to bring greater transparency to the membership process; to set clear expectations and standards for aspiring member companies to meet as a condition of joining the organization; and, above all, to emphasize the complementary and mutually reinforcing nature of combatting terrorism and violent extremism and ensuring respect for human rights.
The BSR report also supports a “big tent” approach to membership, an initiative we have already begun prioritizing with our 2021 strategic objective to take a human rights based-approach to broadening and diversifying membership. By the end of this year, we expect to have doubled the number of GIFCT members since last year’s summit. These members represent an increasingly diverse group of companies, showing that it is not just one kind of platform facing terrorist and violent extremist exploitation. We have also already begun a mapping exercise and recruitment effort to engage with more companies outside of the United States and Europe. If you have recommendations for particular companies that would benefit from a conversation with our team, please share them with us here.
Another key theme in the BSR report to which we have already committed significant time and focus concerns how bias in the form of a disproportionate focus on Islamist extremist content influences GIFCT human rights impacts. As part of our effort to address this bias in the counterterrorism field at large, as well as to capture an increasingly dangerous and diverse array of terrorist and violent extremist content, we have been leading a global multistakeholder review of the taxonomy of GIFCT’s hash-sharing database this year. As the BSR report notes, this project aligns with their recommendations to develop a common understanding of terrorist and violent extremist content, as well as to build that understanding on “behavior” in addition to “groups.” We look forward to releasing a publication on this subject with updates on how we’ll initially expand the taxonomy and chapters from our team, international experts, and civil society stakeholders in advance of the GIFCT Global Summit next week. If you would like to join our panel discussion on the topic, please register here.
A third and final area of progress that I would like to highlight concerns the evolution of GIFCT’s incident response framework and increasing transparency around our work to respond to terrorist and mass violent events and our hash-sharing process. It is our standard practice to disclose information about the Content Incident Protocol (CIP) process and relevant metrics when activated, to conduct a review after the CIP has been initiated, and not to allow governments to add hashes directly to the database. Over the past year, we have worked to enhance transparency about collaboration that occurs for incidents not activating the CIP, as well as how the hash-sharing database functions. We have also emphasized in our refined membership guidelines that companies using the hash-sharing database must have an adequate appeals mechanism and are working on enhancing the capability for remedy when needed.
Other recommendations in the assessment that we have already made progress towards implementing include:
Human rights impacts:
- Conducting a stakeholder mapping to identify organizations and experts that would increase the diversity of rights holders whose voices are heard in GIFCT activities
Terrorist and violent extremist content:
- Participating in efforts to pursue counter-terrorism and violent extremism priorities from an holistic and strategic perspective
Stakeholder engagement:
- Continuing mapping stakeholders to further identify organizations and experts that would increase the diversity of rights holders whose voices are heard in GIFCT activities—and creating plans for their involvement
2. Near- and Medium-Term Commitments (6-12 months)
While we have already begun implementing some of their initial recommendations in the report, there is much work to be done as GIFCT continues to grow and develop in its second year as an independent organization. Over the next six to 12 months, we look forward to making significant progress on implementing the following recommendations:
Mission and goals:
- Create a human rights policy for GIFCT
- Embed a commitment to human rights into other relevant GIFCT governing documents
Human rights impacts:
- Ensure that addressing the full range of GIFCT human rights impacts are embedded into GIFCT’s work plan
- Create a framework for ongoing human rights due diligence
Content removal and preservation:
- Convene multi-stakeholder discussions to advance acceptance and adoption of legal carve-outs for evidentiary content
- Use a GIFCT “common understanding” of terrorist and violent extremist content to determine inclusion in the hash-sharing database in the medium to long term
- Introduce and expand transparency and oversight mechanisms alongside the extension of content in the hash-sharing database
- Establish a multi-stakeholder process to develop metrics on how the hash-sharing database is used
Theory of change and programmatic priorities
- Develop position statements on the rights-based laws, policies, regulations, and strategies needed to more effectively address the exploitation of digital platforms by terrorists and violent extremists
- Proactively express this point of view with relevant governments, policy makers, and regulators
GIFCT membership:
- Establish a tiered membership structure for GIFCT
- Establish a process to (1) expel companies not living up to their membership commitments and / or (2) alter a company’s membership tier
- Actively recruit new member companies, especially from non-US locations
- Actively recruit new member companies from elsewhere along the technology “stack”
- Provide technical assistance to smaller companies to address human rights risks
Stakeholder engagement:
- Establish and maintain closer relationships with the United Nations system
- Train all GIFCT participants in principles of good stakeholder engagement
- Consider geographic diversity when rotating government membership of IAC
Governance, accountability, and transparency:
- Institute a system of formal recommendations from the IAC to the Operating Board, and formal responses from the Operating Board to the IAC
- Publish summaries of minutes of Operating Board and IAC meetings
- Task the IAC with publishing an annual statement about the performance of GIFCT
Organizational issues:
- Create a diversity, equity, and inclusion ambition for (1) GIFCT staff and (2) GIFCT participants
- Continue enhancing GIFCT staff support for the IAC and Working Groups
- Create a GIFCT government and management chart
3. Longer-Term Commitments and Considerations
As the report notes, not all these recommendations can or should be implemented immediately. Rather, it is suggested that GIFCT set out a yearslong plan of continuous improvement. While some of these recommendations will require significant new investment and discussion from GIFCT stakeholder groups about whether and how to move forward, we remain committed to exploring these proposals in earnest over the coming years as the organization, our membership, our programs, and, of course, the global threats from terrorist and violent extremist activity continue to evolve.
Content removal and preservation:
- Require contributing companies to conduct human review and approval prior to adding hashes to the database
- Investigate how to enable third-party reviews of the hash-sharing database to assess whether hashes are consistent with the GIFCT taxonomy
- Develop a process for enabling researcher access to the hash-sharing database and associated content
- Require companies that contribute to and utilize the hash-sharing database to commit to specific disclosure
- Enable multi-stakeholder governance of the hash-sharing database to the extent possible under the current management model (i.e., hosted by Facebook Threat Exchange) and develop a plan for long-term governance and oversight
Governance, accountability, and transparency:
- In two years time, review the merits of transitioning to a multi-stakeholder Operating Board
- Establish a multi-stakeholder process to develop metrics about how the hash-sharing database is used
- Require GIFCT member companies to publish insights into their use of the hash-sharing database as part of their transparency reports, or similar
Organizational issues:
- Establish a mechanism to provide stipends for non-company / non-government participants in GIFCT
- Hire a “Human Rights & Stakeholder Engagement” Director
Let me close by expressing my deep gratitude to the BSR team — Dunstan Allison-Hope, Susan Morgan, and Lindsey Andersen — who have dedicated enormous time and talent to this effort over the past six months. We are also grateful to the dozens of stakeholders around the world who have shared their perspectives and experiences with BSR and GIFCT.
In six months’ time, we will hold an open meeting with our stakeholding community to assess progress against the above outlined preliminary commitments and to solicit ideas and feedback on where there remains room for improvement or modification. In the meantime, my door is always open. In the months and years ahead, I very much look forward to working together as GIFCT draws on this foundational report to embed human rights in our strategy, governance, and activities.