GIFCT invests in the development and distribution of groundbreaking technological solutions to support member companies committed to preventing terrorist and violent extremists from exploiting their platforms while protecting human rights.

Vision
GIFCT aims to equip digital platforms and civil society groups with awareness, knowledge, and technical tools to develop sustainable programs to disrupt terrorist and violent extremist activity online. The threat of terrorism and violent extremism continues to evolve dynamically, similarly, the technology landscape is evolving rapidly as new technology emerges and existing technologies are repurposed and reused in novel ways. The technical solutions we develop must do more than be sustaining, they must evolve to keep pace with the changing landscape.
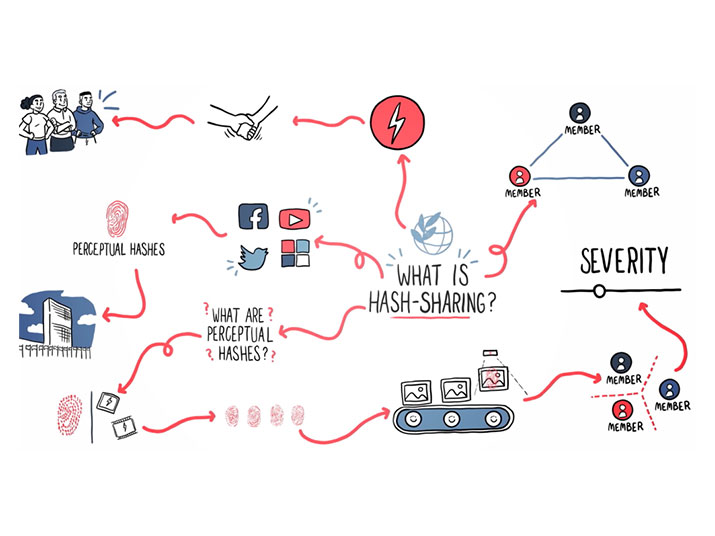
GIFCT's Hash-Sharing Database
The Hash-Sharing Database (HSDB) is currently GIFCT’s leading cross-platform technical solution that allows members to identify if and where terrorists or violent extremists are attempting to exploit their respective platforms. GIFCT enhances and evolves the HSDB to ensure that it is useful, reliable, and effective in keeping pace with the threat. The HSDB is a shared, safe and secure industry database of hashes of known content produced by terrorist entities. Hashes are numerical representations, or digital fingerprints, of content, such as images, videos or PDFs, and cannot be reverse-engineered to recreate the content itself. In practice, the HSDB provides a signal to identify where terrorist and violent extremist activity may be taking place on member’s platforms that violates their policies and terms of service.

Diversifying Value
GIFCT is also looking to the future with our membership continuing to grow with a more diverse range of digital platforms and the need to respond to a changing dynamic set of threats and opportunities. This requires that we diversify the value we add by building baseline capabilities at a trial or prototype level which respond directly to the needs of members and identify new areas of value that we can provide, improving efficiency and effectiveness across the tech sector.
Ethos
How we develop these capabilities is just as important as what we develop. We aim to lead by example, thoughtfully considering the impacts of our technology decisions, evaluating the needs of our different stakeholders and monitoring and measuring the impact of our products to the best of our ability. A human rights based approach is core to GIFCT’s mission and so we design, test and build considering the rights that the systems we develop will impact as well as whose rights will be impacted at every phase of development.
Ultimately, the aim is to contribute to building a stronger, safer, more secure open internet for all users.

Code of Conduct
GIFCT has developed a code of conduct that outlines the expectations for acceptable use of the technology resources that we produce, operate, and maintain. These guidelines are in place to ensure that the tools we deliver are used in a manner that supports GIFCT’s mission and values: to prevent terrorists and violent extremists from exploiting digital platforms and to be transparent, inclusive, and respectful of the fundamental and universal human rights that terrorists and violent extremists seek to undermine.